In the latest release of Windows 2008 R2, Terminal Services has been
renamed Remote Desktop Services (RDS). There are many enhancements in
this release including enhanced multimedia performance and the ability
to publish custom applications sets to specific users through Remote
Desktop Web Access. The Web Access role as the name suggests allows
users to access Remote Desktop applications through a web site. This
feature is official known as RemoteApp. The new name for the core
Terminal Server running in application mode for user sessions is Remote
Desktop Session Host.
In my environment I will configure the Remote Desktop Session Host
and Web Access roles on the same server. I will also install the Remote
Desktop Licensing role on a dedicated server so that any additional
Session Hosts I add in the future can share this service. The License
Server role can be installed on your Session Host server if desired.
All of my servers are members of an Active Directory domain.
Install Remote Desktop Licensing Role
To start go into the Server Manager on the server that will host the Licensing role service.

Under Roles Summary select “Add Roles”.

Click Next.

Check Remote Desktop Services and click Next.

Click Next.

Check Remote Desktop Licensing and select Next.

Discovery scopes are no longer used for licensing with Windows 2008
R2 Remote Desktop, we can assign these to our Remote Desktop Session
Host manually or through a group policy. There is a 120 day grace
period allowed for connections to a Remote Desktop Session Host before a
license server needs to be activated. Click Next.

Confirm the settings and click Install. Then click Close once the install is completed.
Install Remote Desktop Session Host and Web Access Roles
Now switch to the server that will be our Remote Desktop Session Host and Web Access server. Start Server Manager.

Select “Add Roles”.

Check Remote Desktop Services and click Next.

Check the RD Session Host and RD Web Access services. When you add Web Access you’ll be prompted:
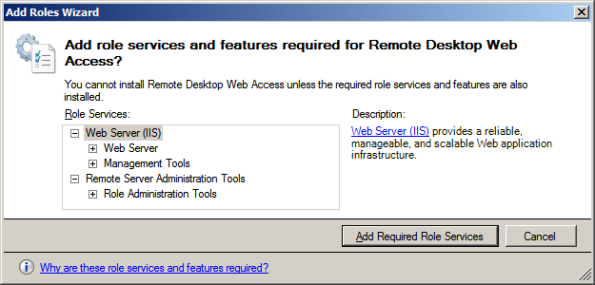
Click Add Required Role Services to accept to install the prerequisites. Then click Next back at the Add Roles Wizard.

At this time I’ll select “Do not required Network Level
Authentication”. There are some issues using NLA if we have Windows XP
SP3 clients, but there is a registry fix available. Click Next.

I’ll choose Per User licensing mode and click Next.
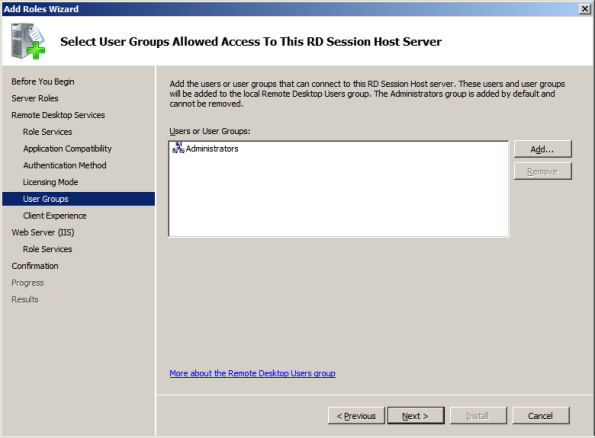
Now we can add additional groups of users to have access to
applications on the Session Host. The local Administrator group on the
server is included by default. I’ll add additional groups later so for
now I’ll click Next.

I’ll check all of the available check boxes to provide for an
enhanced client experience on this Session Host. This will allow for
capabilities such as playing multimedia through the RD session and
Windows Aero if we publish a full desktop on this server. This all
sound great, but be aware that these features will consume additional
resources on your Session Host. Click Next.

Click Next, then click Install at the confirmation screen that
follows. The server should prompt for a reboot when the installation is
complete.
Configure Session Host to Use Licensing Server
After you reboot and log on to your Session Host and go to Start >
Administrative Tools > Remote Desktop Services > Remote Desktop
Session Host Configuration.

In the middle pane under Licensing double click “Remote Desktop license servers”.
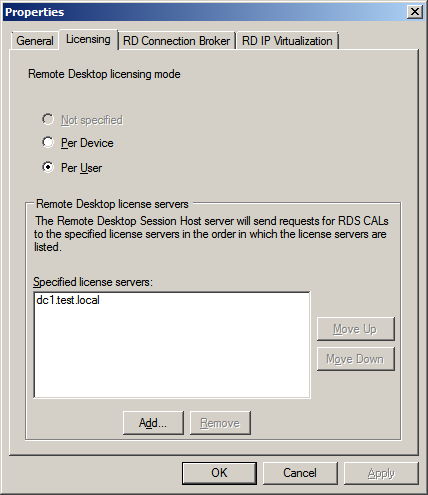
Click Add.

Your license server should appear under known license servers. If
not, enter the FQDN or IP address of the server and click Add. If you
are not logged on as a Domain Administrator and the License server is on
a different server in your domain it will give you a warning about
being unable to verify, it should be okay to simply click through this
message. Click OK.
Add Users for Remote Desktop on the Session Host
Now we’ll go into Computer Management and add the additional users
group(s) that we want to allow access to Remote Desktop sessions on the
Session Host. Go to Start > Administrative Tools > Computer
Management.

Open up “Local Users and Groups” on the left pane, then highlight the
Groups sub-folder. Double click the “Remote Desktop Users” group in
the center.

I’ll add the Domain Users group. Click Add.

I will allow all of my domain users access to Remote Desktop
sessions, so I’ll type Domain Users, click Check Names, then click OK.
Click OK through the remaining dialog windows, and close Computer
Management.
Publish a Remote Desktop RemoteApp Program
Now it’s time to publish a test application. Go to Start >
Administrative Tools > Remote Desktop Services > RemoteApp
Manager. Click “Add RemoteApp Programs” in the right Actions pane.

Click Next.
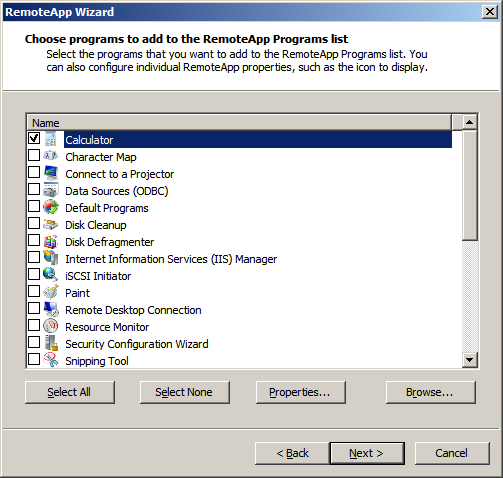
I’ll test using the Calculator, so check that and click Next. At the confirmation window click Finish.
Test Newly Published RemoteApp Program
Now I’ll log on to a client machine in my domain to test the newly
published Calculator. On the client open up Internet Explorer and enter
“
http://YourWebAccessServer/rdweb”.
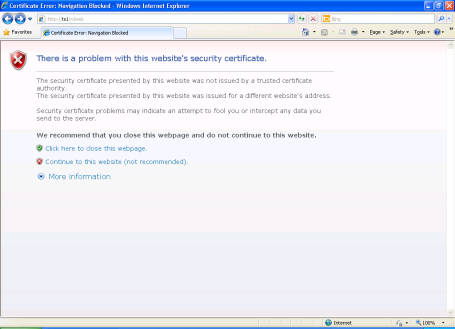
Click “Continue to this website” in the browser window.

You may receive a warning about the ActiveX control not being
installed. I’ve generally only seen this on Windows XP clients. To fix
this reset your IE internet settings by clicking Tools > Internet
Options.

Click the Advanced tab. Then click the Reset button. Click through
the dialog boxes. Once you’re back at the IE browser windows, close IE
and reopen it. Now you go back to “
http://YourWebAccessServer/rdweb” and click through the certificate warning you should be presented with the RD Web Access log on screen.
When a user with standard privileges on the client accesses the RD
Web Access site for the first time they will receive a warning about
installing the Remote Desktop ActiveX Control. Confirm that you trust
the web site address you are contacting. You probably will because you
should be accessing your own server!

Click the warning message at the top and select Run Add On.

Now click Run.
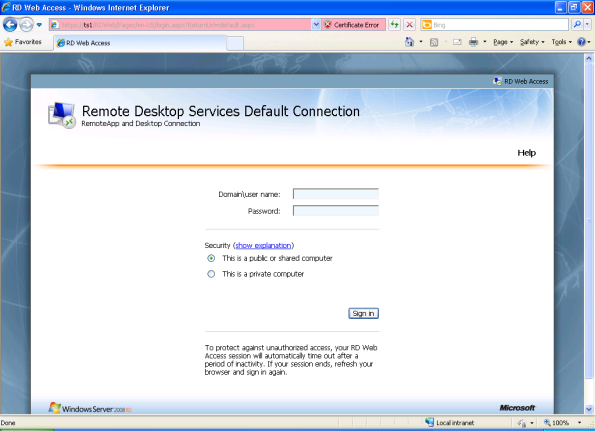
Log on with a user you’ve given access to Remote Desktop sessions.
The administrator should automatically be given access. Be sure and
specify the domain first if you are using a domain account.

You’ll receive a warning about unable to identify the remote connection publisher, click Connect.
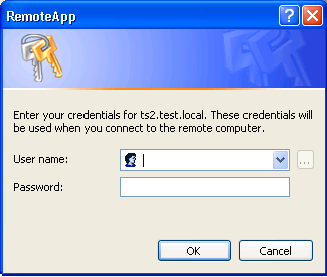
It will now ask for you to log on to the the RD session. Enter the user name in the Domain\Username format.

And another warning will appear about identity verification, click
Yes. We’ll set up a new certificate from a trusted certificate
authority later to eliminate this message. The RemoteApp should now
launch.
Eliminate Certificate Warnings (optional)
Now let’s work to eliminate the multiple certificate warnings we
receive when accessing our Remote Desktops and RemoteApp programs. In
this example I will make use of an enterprise certificate authority
configured in my AD domain, of which my RD Session Host/Web Access
server is a member.
Note that this process will only eliminate the warnings if my clients
and RDS server are members of the AD domain since they will
automatically trust the AD enterprise certificate authority. If you
have non-domain clients that connect to your RDS server you’ll need to
export and import your CA root certificate into the certificate store on
these systems so the IIS and RDS certificates are trusted. Page 1 of
the post
Configuring Non-Domain Windows IIS Servers has details on how to do this.
Eliminate RD Web Access/IIS Certificate Warning
First if you have not done so in your environment already,
Install an Enterprise Certificate Authority in Windows 2008 R2.
Next,
Configure a Server Certificate for IIS/RD Web Access.
These two steps should take care of the warning we receive when we access the RD Web Access web site.
Eliminate RemoteApp Certificate Warning
Now let’s remove the first RemoteApp certificate warning. On the
Session Host navigate to Start > Administrative Tools > Remote
Desktop Services > RemoteApp Manager.

Under Overview click Change after the Digital Signature Settings heading.

Under the Digital Signature tab check the box for “Sign with a digital certificate”. Then click the Change button.

Select the certificate published from our enterprise CA. I’ll use
the certificate I requested for my IIS/RD Web Access service. Be sure
and choose the certificate issued by the CA and not the self signed
certificate. Click OK.

Click OK back at the RemoteApp Deployment Settings box.
Once a certificate from a trusted certificate authority is
configured, the RemoteApp session should pass through the authentication
credentials entered on the RD Web Access page and the second log on to
the Session Host will no longer be necessary. Yes!
Eliminate Remote Desktop Connection Certificate Warning
I have noticed that this step is not needed with Windows 7 domain
member clients, but for good measure I wanted to make sure that all of
my potential clients are cleared of certificate warning messages. On
the Session Host go to Start > Admin Tools > Remote Desktop
Services > Remote Desktop Session Host Configuration.

In the center pane under Connections double click the RDP-Tcp connection.
In the General tab under Certificate click the Select button.
Again I’ll use the certificate I published for the IIS/Web Access role. Click OK.
Back at the RDP-Tcp Properties box click OK. We should now be
configured to access our RemoteApps without any more annoying
certificate warnings!
















































